Secrets Behind the Screen
Ever wonder how a single line of code can open vaults?
Or how digital phantoms vanish with millions, leaving no trace?
Real hacks, AI gone rogue, and the fragile web beneath our world

State-Sponsored Shadows
North Korea’s Lazarus Group slipped into the digital vaults of Axie Infinity and disappeared with over $600 million. No alarms. No arrests. Just code, cash, and cold silence.

Can Hackers Outsmart the World’s Most Secure Systems?
In February 2016, shadowy hackers infiltrated the systems of Bangladesh’s central bank, initiating one of the most audacious cyber heists in history.While most of the transactions were blocked, $81 million vanished into the digital void, leaving investigators scrambling to trace the money.

Teenagers with Root Access
One slip in Twitter’s admin tools gave hackers global megaphones. What followed was a Bitcoin scam broadcast from the world’s most powerful voices. This isn’t fiction — it happened.

The Code Thinks for Itself
AI is no longer just a tool. It’s a weapon. From auto-generating ransomware to deepfaking CEOs, here’s how machines are entering the battlefield of digital crime.

Hackers vs. Global Enterprises
The LockBit group has rapidly become one of the most notorious ransomware gangs, carrying out sophisticated cyberheists against some of the world’s largest organizations. Known for their highly organized operations and the use of double-extortion tactics, they have demanded millions of dollars in ransom, causing widespread disruption and damage to critical systems.
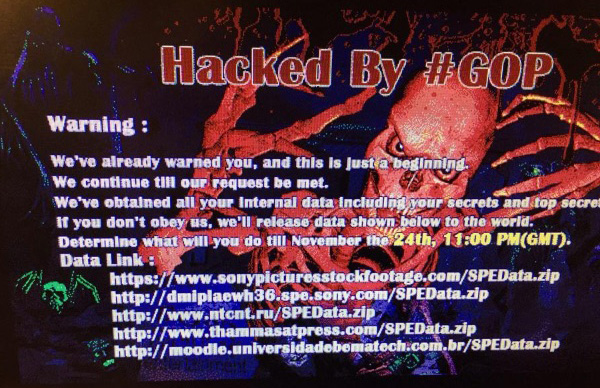
Where Politics Meets Payloads
When Sony released a movie mocking a dictator, hackers unleashed hell — leaking emails, films, and secrets. This was more than a breach — it was a message. The attack exposed the inner workings of Hollywood, revealing private deals, celebrity paychecks, and unfiltered executive communications. It also marked a turning point, as studios began to rethink their security measures and the risks of crossing politically sensitive lines. But behind the data dumps was something deeper — a warning wrapped in silence. No fingerprints. No clear demands. Just chaos, fear, and a question that still lingers: who’s really pulling the strings? And if art can provoke war… what else can it ignite?
Is Your Data truly safe?
In 2020, a massive internet outage caused by a single misconfigured router brought down major websites and services worldwide. This incident highlighted how fragile our digital infrastructure can be, reminding us that even the smallest mistakes can have catastrophic consequences on a global scale.
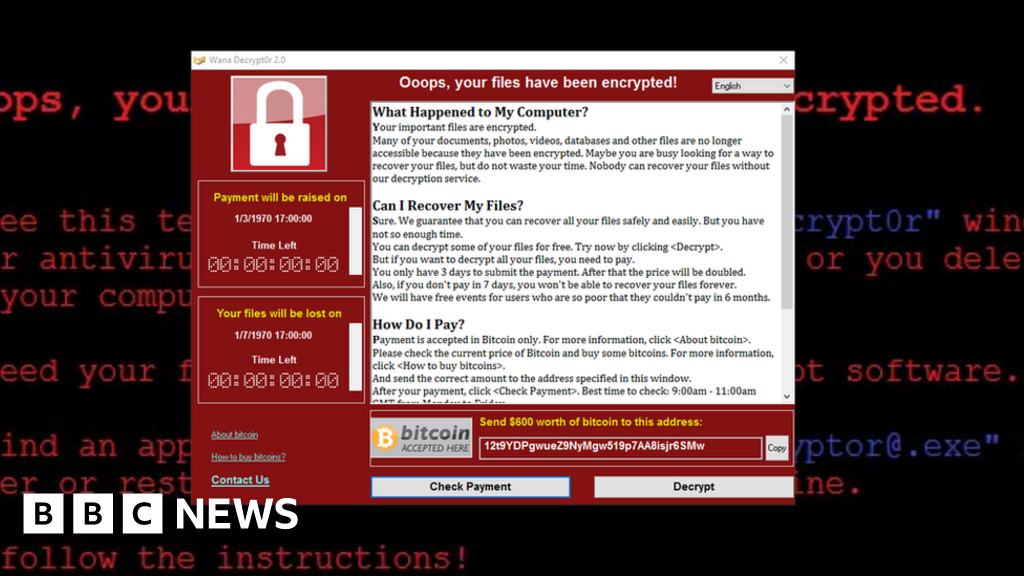
Is Your System Truly Secure?
In May 2017, the WannaCry ransomware attack crippled over 200,000 computers across 150 countries, including critical systems in the UK's National Health Service (NHS). The ransomware encrypted files on infected machines, demanding $300 in Bitcoin for their release. The attack exploited a vulnerability in Microsoft Windows. Hospitals across the UK were forced to cancel surgeries and turn away patients, causing widespread chaos.
Decrypt the Unseen. Expose the Untraceable.

Bitcoin, Blockchain & a Couple on the Run
In 2016, hackers stole 119,000 Bitcoins from Bitfinex. The crypto lay dormant until it resurfaced years later — leading to the wild arrest of a rapper and her techie husband. Turns out, they couldn’t even spend most of it.

The Real-Life Goodfellas Job
In 1978, a mob-connected crew hit JFK airport and vanished with $5M in cash and jewels. It was so cinematic, it inspired Goodfellas. But in real life? Most of the thieves disappeared — forever.
Where Flow Becomes Fracture
Vibe coding glorifies instinct over discipline, intuition over standards. And when you break the syntax once too often — things fall apart. APIs crumble. Logic bleeds. Bugs hide in the vibe, waiting to blow production at 3AM.

Crypto, Cartoons & a $625M Vanish Act
In March 2022, over $625M vanished from the Ronin blockchain — the same one behind the play-to-earn game Axie Infinity. The craziest part? Nobody noticed... for six days. U.S. officials say North Korean hackers pulled the job. Others think it was an inside job. All we know is: someone got very rich — and very quiet.

One AI Image, Global Panic
In 2023, an AI-generated image of an explosion at the Pentagon went viral. Markets crashed, news sites scrambled, and chaos ensued — all because of one fake tweet.

AI Voice, Real Theft
Using AI, scammers cloned a CEO’s voice and tricked an employee into wiring $243K. It sounded so real, no one questioned it. By the time they found out, the money was long gone.

The Web’s Weakest Link
In 2022, internet cables under the sea were cut near France — causing major disruptions across Europe. No one saw it coming. It showed just how easily the internet can snap.

Your Wi-Fi, Their Weapon
In 2016, hackers used ordinary home routers to create a massive botnet that crashed Netflix, Twitter, and Reddit. Millions had no idea their devices were part of the attack.

Yes, “123456” Still Works
In 2023, hackers broke into government accounts using weak passwords like "Password1". No malware. No phishing. Just lazy security and bad habits.

From Hobby to Hack-Back Hero
Think you need a CS degree to join the digital frontlines? Think again. Discover how you can go from zero to cyber-slayer — and get paid to protect the web’s darkest corners.